Exploring Security Vulnerabilities with Rubber Ducky, OMG Cables, and More at Ctrl+Alt+Delightful
In an increasingly complex world of cybersecurity, events like Ctrl+Alt+Delightful bring together some of the brightest minds in the IT space. Hosted by ThreatLocker in Orlando, this gathering was a deep dive into modern threats, featuring a hands-on hacking demonstration by Danny Jenkins, CEO of ThreatLocker. From USB-based attacks to exploiting key system vulnerabilities, this event offered attendees a clear view of the real-world risks businesses face—and how to defend against them.
The Rubber Ducky Attack: A Simple Yet Effective Threat
The presentation kicked off with a live demonstration of a Rubber Ducky hack. For those unfamiliar, the Rubber Ducky isn’t a bath toy; it’s a disguised USB device that acts as a keyboard when plugged into a computer, capable of executing pre-programmed commands at lightning speed.
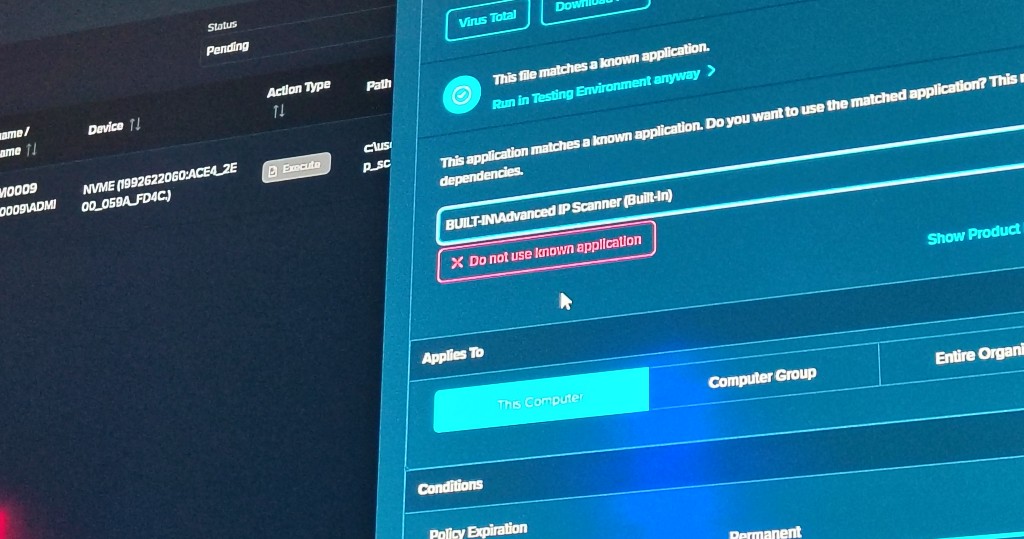
Danny began by explaining how these attacks are successful. He noted, “If you can physically access a machine, you can plug in a Rubber Ducky and bypass common security measures like USB blocking.” He demonstrated by plugging one into a victim’s computer, running simple commands that ultimately uploaded sensitive data, like passwords and salary information, to a remote Google Cloud repository. This subtle attack left no trace on Windows Defender, showcasing how dangerous even a brief physical access point can be.
A particularly chilling story involved an offer of $500,000 to a Tesla employee to use one of these devices to breach the company’s security. Although the employee didn’t take the bribe, the story highlights the potential risks companies face when internal actors are tempted by financial incentives.
The OMG Cable: Invisible Wireless Hacking

The OMG Cable was the next highlight of the demonstration. This innocuous-looking device resembles a regular iPhone or USB-C cable but contains a hidden wireless antenna. It allows a hacker to send keystrokes to a machine remotely, after simply plugging it in.
Danny shared a case where he breached a medical facility’s network using an OMG Cable. By pretending to drop his phone behind a computer and subtly plugging the OMG Cable into the victim’s machine, he gained wireless control of their systems, eventually extracting sensitive medical data. This method of attack emphasizes the importance of physical security, as even something as harmless-looking as a phone charger can be a hacker’s gateway into critical infrastructure.
Zero Trust: The Future of Cybersecurity
A key part of the event was the discussion on ThreatLocker’s approach to security—namely, the shift from default-allow to default-deny security models. Danny explained, “Today, most security systems allow everything unless it’s flagged as bad. At ThreatLocker, we’ve flipped the script. Our goal is to block everything unless it’s explicitly needed.” This zero-trust approach eliminates gaps that hackers typically exploit.

Danny outlined ThreatLocker’s journey, starting with three founders in Orlando in 2017, to now supporting over 50,000 companies, including major organizations like JetBlue, parts of the U.S. Navy, and hospitals across the globe. The growth of ThreatLocker is a testament to the importance of adaptive, modern cybersecurity practices.
The Flipper: A Hacker’s Swiss Army Knife
One of the most exciting parts of the demonstration involved the Flipper, a multi-functional device capable of everything from emulating Bluetooth signals to unlocking car doors. Danny showcased how it can even spoof Apple AirPods, connect to a MacBook, and send keystrokes to the machine without raising any alarms.
In a live demo, Danny used the Flipper to hijack a MacBook by mimicking the AirPods’ Bluetooth signal and sending keystrokes. This resulted in complete system control, allowing the team to open a terminal, download a reverse shell, and extract data—all without the user clicking a single prompt.
Interesting side note: I actually won the flipper used in the demo! I’ll be sure to reset it to factory settings before using though! 😉
The Importance of Controlled Simulations
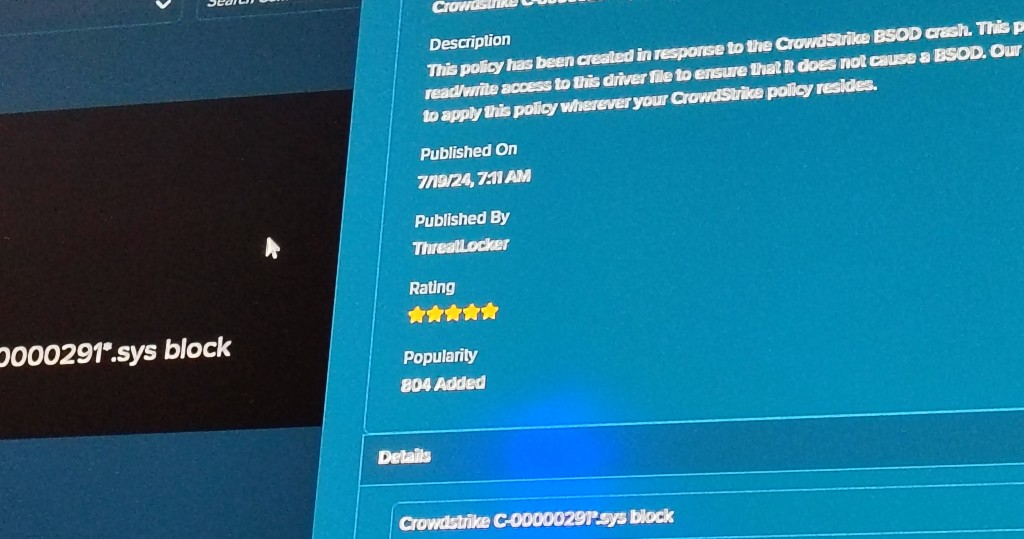
ThreatLocker emphasizes the need for controlled testing environments, allowing organizations to simulate attacks without causing real damage. Danny demonstrated ThreatLocker’s simulation mode, which learns and adapts to an organization’s unique needs, ensuring zero-trust policies can be implemented without interrupting operations. He also showcased how this mode allows users to monitor potential threats before they happen, helping to identify weak points before hackers can exploit them.
Final Thoughts: Cybersecurity is More Than Just Software
Throughout the event, the overarching message was clear: cybersecurity is not just about having the right software in place. It’s about understanding the full scope of your infrastructure’s vulnerabilities—from physical threats like Rubber Ducky and OMG Cables to internal threats and sophisticated attacks like the Flipper.
As Danny pointed out during the demonstration, “You don’t need administrative access to cause damage. Simply gaining regular user access can often be enough to steal critical data or deploy ransomware.” It’s a sobering thought, but events like Ctrl+Alt+Delightful remind us that staying ahead in cybersecurity requires constant vigilance, testing, and the adoption of a zero-trust model.
If you’re looking to learn more about these threats and how to protect your organization, ThreatLocker has made several educational webinars available on their YouTube channel, including deep dives into Rubber Ducky hacks and OMG Cables.
Conclusion
Ctrl+Alt+Delightful was a powerful reminder of the ever-evolving threat landscape and the importance of adopting a proactive, zero-trust approach to cybersecurity. Whether it’s through a seemingly harmless USB drive or a disguised cable, the potential for system breaches is real, and it’s essential for businesses of all sizes to stay informed and prepared.
